Microsoft—and Ars—advise split-tunnel VPNs to minimize coronavirus woes
-
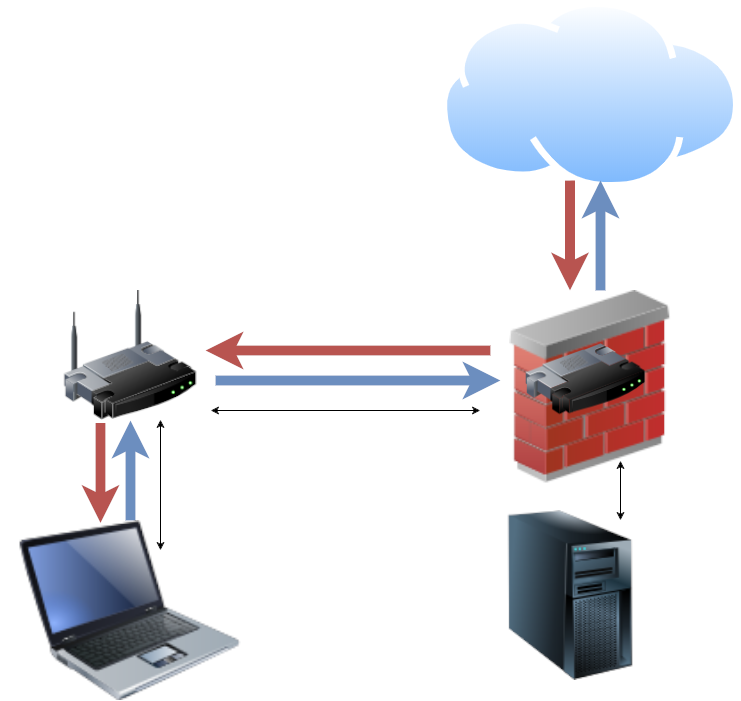
The traditional office VPN routes not just internal office traffic, but all traffic—including internet traffic—across an established VPN. [credit: Jim Salter ]
When SARS hit its peak, remote work wasn't yet practical enough for quarantine efforts to affect office networks much. With the coronavirus, though, most of the toolset needed to work from home or the road is available—but many office networks are having difficulty handling the sudden increase in scale.
Internet scale versus VPN scale
There's not much you can do about a WAN (Wide Area Network) connection that isn't robust enough to handle traffic from remote workers to internal infrastructure such as file servers and application servers. But much of a typical company's infrastructure isn't onsite at all anymore—it's increasingly likely to be hosted in the cloud, behind its own set of protective firewalls and filters.
Traditionally, most office VPNs are set up to route not just office traffic, but all traffic—including Internet-destined traffic—across the user's VPN tunnel. For most sites, that means paying a double penalty—or worse—for all Internet traffic from VPN-connected users. Each HTTPS request and its subsequent response must hit both the upload and download side of the office's WAN twice. This is bad enough with a symmetric WAN—e.g., a 500Mbps fiber link—but it's beyond punishing for an asymmetric WAN, such as a 100Mbps-down/10Mbps-up coaxial link.
Read 6 remaining paragraphs | Comments
https://ift.tt/2TEObT2
from Ars Technica https://ift.tt/2TFBLKr

No comments